This will be a single post to look at two of the VCP-NV objectives around NSX firewall services. There are two firewall deployments available in a NSX solution – the edge firewall which addresses north-south traffic at the perimeter and the distributed firewall, which focuses on east-west traffic. These firewall types can be deployed together or independently depending on need.
The NSX Distributed Firewall
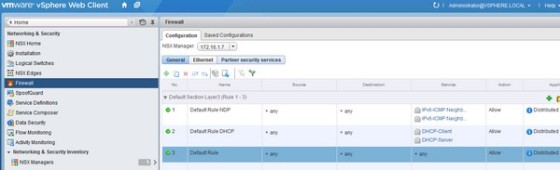
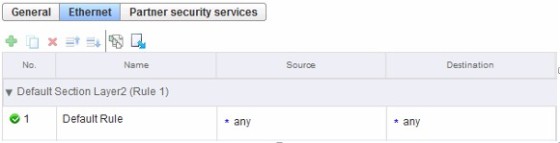
The distributed firewall allows you to create both L2 and L3 rules. By default, all traffic is allowed to pass through all clusters in the infrastructure. This rule cannot be removed (however it can be changed to a ‘deny’) and will always be the ‘bottom’ rule in the firewall ruleset. When new rules are added, they are added above the default rule. Rules are processed from top to bottom.
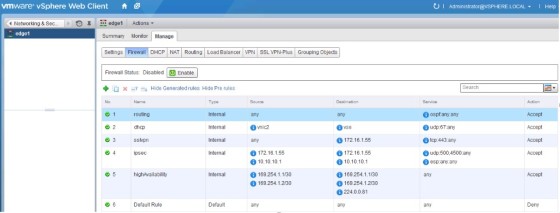
You can view the firewall rules in the vSphere Web Client under ‘Networks and Security’ then ‘Firewall’:
For the default rule you can only change the ‘Action’ and the ‘Logging’ attribute. To change the action, hover the mouse in the top right corner of the action field, then click the ‘Plus’ icon. A dialog box will open, where you can change the setting:
You can add a new rule by clicking the green ‘plus’ symbol. Ensure you are on the General tab if you want to add a L3 rule, and on the Ethernet tab, if you want to add an L2 rule.
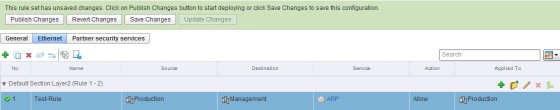
In the example here, I have created an L2 rule allowing ARP traffic between my Production and Management clusters (note that only Layer 2 protocols can be used in a L2 firewall rule):
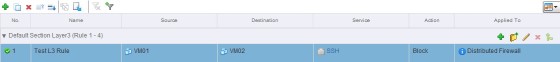
And this one is an example of a L3 rule, between 2 virtual machines:
This rule will block SSH traffic from VM01 to VM02. When creating a rule you have multiple options for the objects in scope, which includes clusters, virtual machines, vNics and resource pools:
After creating a rule, the changes will need to be published before they take effect. If required you can change the order of the rules, using the up and down arrows:
After changing the order, the changes will need to be published.
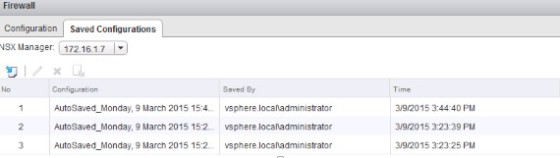
It’s possible to export the firewall configuration as an .xml file – this can then be imported at any point from the ‘Saved Configurations’ tab:
Notice that there are ‘auto saved’ configurations, from which you can revert changes if necessary.
NSX Edge Firewall
NSX Edge firewall services are provided by an edge services router. It’s settings are managed under the ‘Firewall’ tab on the edge router:
The edge firewall is disabled by default. When enabled, there is a default ‘deny’ rule that will block all traffic, other than those specified in the other existing rules. As with the distributed firewall, custom rules can be created (though only Layer 3 rules can be created on the edge router). As with the distributed router there are a number of objects which you can build your firewall rules around, including Resource Pools, Virtual Machines, vApps, vNICs and Clusters:
SpoofGuard
I just wanted to finish this post by talking about SpoofGuard, although it doesn’t appear to be specifically referenced on the VCP-NV blueprint. Spoofguard is a feature that can prevent unauthorized IP address assignments.
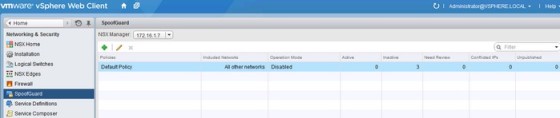
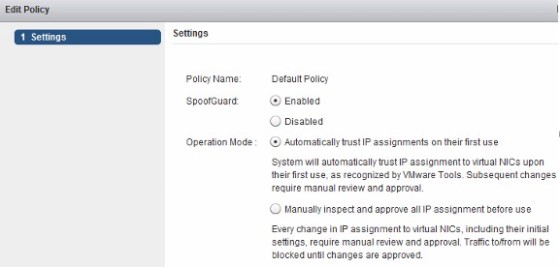
SpoofGuard allows you to authorize IP addresses learnt from Vmtools. When SpoofGuard is enabled, only virtual machine’s whose IP address is approved are allowed to communicate. It is disabled by default, so all traffic is allowed. To enable it on all networks, you can edit the default policy (or create a new one, to select the networks in scope):
When it is enabled, there is a choice to make regarding how IP addresses are learned. You can either have all IP addresses trusted the first time they are seen (they will become untrusted if the VMs IP is changed), or you can choose to manually authorize each IP address.
Useful Links and Resources
https://pubs.vmware.com/NSX-6/topic/com.vmware.ICbase/PDF/nsx_6_admin.pdf