Following on from my previous post, which looked at configuring the NSX SSL VPN-Plus, this post will look at the other two VPN types available with NSX – IPSec VPN and L2 VPN. The administration guide covers both in detail and is recommended reading if you’re studying for the VCP-NV certification. This post will run through the basic configuration steps required for each, starting with the IPSec VPN feature.
Configuring NSX IPSec VPN
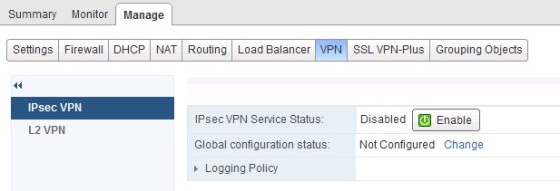
It’s a straight forward task to enable the IPSec VPN service. When looking at the settings for the NSX edge router, select the ‘Manage’ tab then ‘VPN’ sub-tab, then the ‘IPSec VPN’ menu item. Click the ‘Enable’ button, and then publish the changes:
The next step is to configure the global parameters for the IPSec VPN service. In the ‘IPSec VPN’ screen, click ‘Change’ – the global configuration settings window will open:
Here we set the pre-shared key (PSK) and the SSL certificate that will be used for certificate authentication. You will need to have imported a certificate first, before it is available here. After clicking OK here, you will need to publish the changes. The status should now change to ‘Configured’.
The next step is to configure the settings for the IPSec VPN. In the ‘IPSec VPN’ screen, click the green ‘plus’ to begin:
Firstly, type a name for the VPN. The set the Local ID and the Local endpoint. The Local ID will be the Peer ID used on the remote site – this is the public address of the gateway. The Local Subnets are the subnets you are going to give access to via the VPN. Next, enter the Peer ID, Peer IP and the IP addresses of the peer subnets (in CIDR format). Guidance on what should be used in each field can be found here.
Next, select the encryption algorithm to be used, and configure the authentication options. Once complete, click OK – the edge router will then attempt to bring up the VPN tunnel.
The ‘Show IPSec Statistics’ link can be used to check the tunnel status:
Configuring L2 VPN
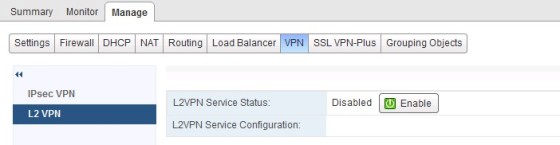
The L2 VPN allows you to create a tunnel between two sites, to allow you to ‘stretch’ a subnet across locations. To enable L2 VPN functionality, in the settings for the edge router, go to the manage tab, then VPN tab then click ‘L2 VPN’. Click the ‘Enable’ button:
We now need to configure the L2 VPN on this edge router to either be a client or a server for the L2 VPN connection. When linking two sites together using the L2 VPN, the edge router in one site will act as the server, whilst the other will act as the client.
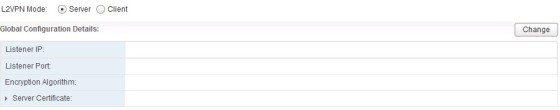
To configure the Server settings, first select the ‘Server’ radio button, then click change:
Now we can set which IP address the VPN server will listen on, the port, the encryption algorithm and the certificate to be used:
Next, under ‘Site Configuration’, we need to add a peer site:
In the ‘Stretched Interfaces’ setting, select the trunked interface that will be ‘stretched’ via the VPN. Once done, click OK then publish the changes.
If we were configuring the router as a client rather than server, the configuration is similar, except rather than setting the user and password for the VPN, we would enter the settings specified on the server:
Useful Links and Resources
https://pubs.vmware.com/NSX-61/index.jsp#com.vmware.nsx.admin.doc/GUID-6152B56B-2119-48E7-B2F2-BDDCF58B3F14.html
https://pubs.vmware.com/NSX-61/index.jsp#com.vmware.nsx.admin.doc/GUID-7977542E-C4BA-484A-9811-1233E2401A23.html