Along with Load balancing, VPN and routing services, an NSX Edge router can also provide DHCP, DNS and NAT services. This post will look at how to configure and manage each, starting with DHCP.
Configuring DHCP on a NSX Services Gateway
An NSX Edge Services Gateway can act as a DHCP server, providing IP addresses to virtual machines on NSX defined networks. It can also be configured as a DHCP relay server, in which case it will forward requests to an external DHCP server. To configure DHCP, go to the ‘Networking and Security’ pane in the vSphere web client, then go to ‘NSX Edges’ and double click on the Edge instance you wish to configure. Once there, click on the ‘DHCP’ tab:
Before enabling DHCP, a DHCP pool should be created. To do so, click the green ‘plus’ symbol:
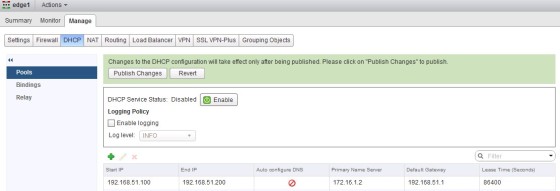
Here you configure the usual DHCP pool options such as the IP pool range, DNS servers, and the default gateway. Once complete, click OK, and then publish your changes:
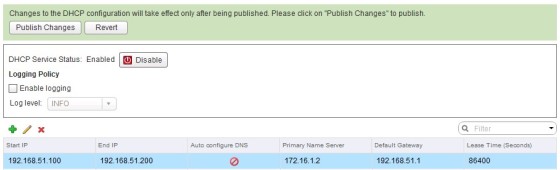
With a pool created, the next step is to enable DHCP. To do so, click the ‘Enable’ button, then publish the change:
And that’s it for the DHCP pool creation. It’s also possible to set DHCP reservations within the scope/pool by going to the ‘Bindings’ menu item and configuring a static mapping:
Enable and Configure DNS Services
The DNS settings for the Edge router can be found on the ‘Settings’ tab then the ‘Configuration’ sub-menu item. Under DNS click ‘Change’:
The router can then be configured to forward DNS requests to an upstream DNS server if required. The edge router will cache DNS requests from the virtual machines. Optionally, enable logging for the DNS service.
Configuring NAT
Another feature that the edge services router is network address translation, or NAT. One use of NAT is when using the NSX load balancing feature, however you can also create NAT rules manually. Source NAT is a common use case, where a internal IP address, is masked behind an external interface on the router.
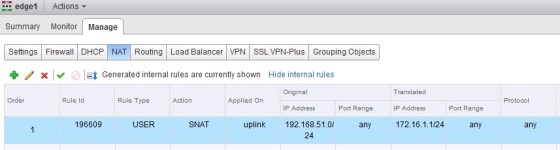
To create a source NAT rule, navigate to the edge router in the web client, then select the NAT tab:
Click the green ‘+’ symbol to begin adding a new rule. You will be prompted to add either a DNAT rule or an SNAT rule:
You’ll be presented with the following window:
The ‘Applied On’ setting refers to which interface on the router the translation will take place. You can then enter the original and translated IPs, or ranges. You can optionally enable logging. When happy, click in the Enable box to enable the rule, then click OK. The changes then need to be published before they take effect. Once done, you should now see the rule in the NAT pane:
A DNAT, or Destination NAT, is added in the same way, however there are a few more options to set. DNAT is used to present an internal server, such as a mail server, to the external network, using an IP address on the router. Below is an example of a DNAT rule, forwarding RDP to an internal server:
That’s all for this post. My next one on VCP-NV will look at configuring and managing VPN services on NSX.