The vSphere Security Guide makes a number of recommendations around best practices for virtual machine security. There are also the vSphere hardening guides, which can be found here.
Installing Antivirus Software
It is recommended that, where required, antivirus is installed within the virtual machines guest operating systems. For virtual machines that have AV installed it is recommended that scheduled scans are staggered in order to prevent performance issues that can occur when a large number of VMs on a host are scanning at the same time.
Limiting Exposure of Sensitive Data Copied to the Clipboard
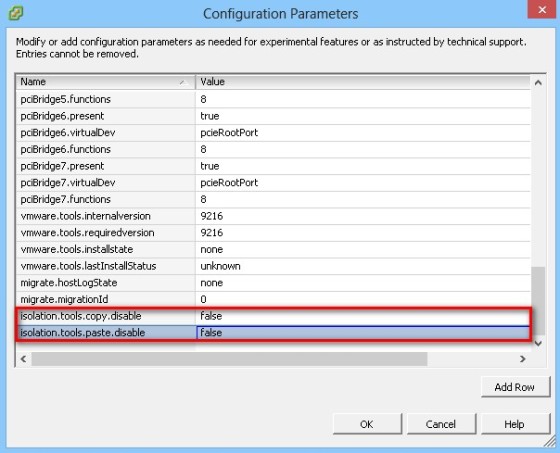
By default, copy and paste operations are disabled. If copy and paste functionality is enabled, you are able to copy and paste between the machine running the console and the guest operating system.
This functionality is controlled with two advanced settings, on a per-virtual machine basis:
Be aware that these advance settings can only be changed when the virtual machine is powered off.
Removing Unnecessary Hardware Devices
It is recommended that any unused virtual hardware is removed from virtual machines, as unused hardware could be used to breach virtual machine security. For example, a CD-ROM drive attached to a VM may be used to access information on the mounted ISO/attached drive.
As an alternative to removing a device, you could prevent a user from connecting or disconnecting it through the guest OS by editing the virtual machine’s VMX file, entering the following line:
device_name.allowGuestConnectionControl = "false"
Limiting Guest Operating System Writes to Host Memory
The guest operating system processes send informational messages to the host using VMware Tools. If the amount of data the host stored as a result of these messages was unlimited, an unrestricted data flow would provide an opportunity for an attacker to stage a denial-of-service (DoS) attack. By default By default the VM can send only 1MB of these messages, however this can be changed. If this was un-restricted then it could be possible for an attacker to write software to send data with the aim of causing DoS.
The setting to configure this behavior is:
tools.setInfo.sizeLimit
It is configured on a per-VM basis. You can increase the guest operating system variable memory limit if large amounts of custom information are being stored in the configuration file. You can also prevent guests from writing any name-value pairs to the configuration file. To do so, use the following setting, and set it to ‘true’:
isolation.tools.setinfo.disable
Configuring Logging Levels for the Guest Operating System
Virtual machines write to a log file on the datastore where the VM is located. An attacker could cause this log file to grow, with the intention of causing a denial of service, by generating events that will be committed to the log file. In order to prevent the possibility of this happening you can configure logging settings for a virtual machine to limit the total size and number of logs that are created. A new log file is created when the host is rebooted – so these files can grow to be quite large. VMware recommend that 10 log files should be retained, each with a maximum size of 1ooKB. This is configurable by adding/changing the following lines in the virtual machine’s VMX file:
log.rotateSize=maximum_size
log.keepOld=number_of_files_to_keep
You can also disable logging entirely for a virtual machine: