As stated in the administration guide, NSX supports a number of different types of VPN. These are:
- SSL VPN-Plus – To allow end users to connect to applications/services
- IPSec VPN – Providing connectivity between sites
- L2 VPN – Allows you to configure a tunnel between sites in order to ‘stretch’ L2 networks
This post will look specifically at giving an overview of configuring SSL VPN-Plus – look out for an upcoming post covering the other two types of VPN.
Configuring SSL VPN-Plus
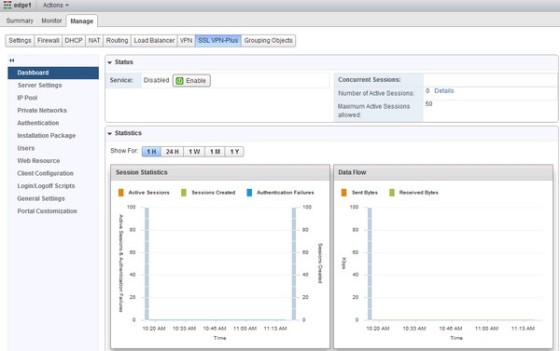
There are a number of steps required to get SSL VPN-Plus set up. The first is to enable SSL on an interface on the edge router. To do so, in the settings for the edge router, go to the SSL VPN-Plus tab:
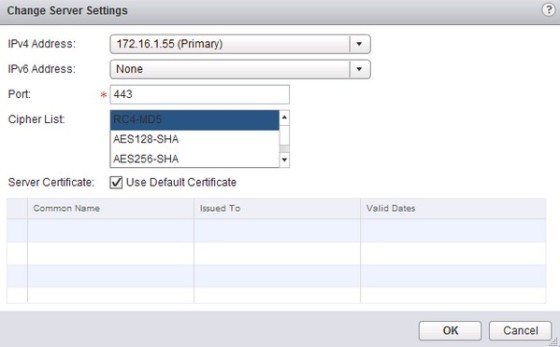
First of all, the server settings need to be configured. Select ‘Server Settings’, then click Change, and select the interface to use, the port and the encryption type:
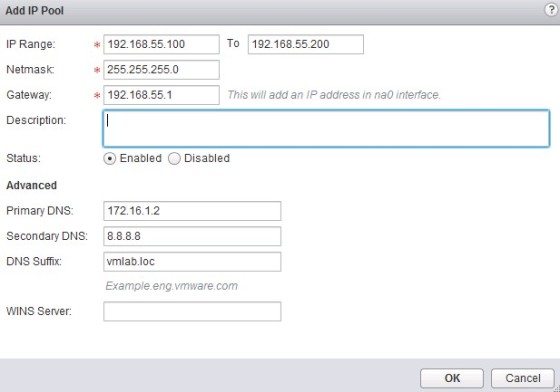
Next, an IP pool needs to be created. When a user successfully connects to the VPN, they will be assigned an address from the pool. Select ‘IP Pools’ from the menu on the left of the screen, and configure an appropriate range:
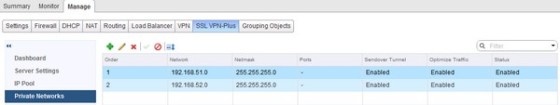
With the IP Pool created, next a Private Network needs to be added. The Private Network settings determine which networks a user can access once connected to the VPN. Select the ‘Private Networks’ menu iten, then click the green plus symbol to begin adding a new private network:
All the networks that the VPN users will need access to should be added:
Next, the authentication methods need to be configured. Click the ‘Authentication’ menu item. Click the green ‘plus’ icon to add an authentication server. There are different options for the type of authentication server to add. These are Active Directory, LDAP, Radius, RSA-ACE and LOCAL. For the purposes of this article I will be using local authentication:
As I have chosen to use local authentication I need to create a user. To do so, head to the ‘Users’ menu item, where you can add local users.
After configuring the authentication settings, the next step is to add an Installation Package. This is the endpoint client software that will be deployed to the remote user. Click on the ‘Installation Package’ menu item. As always, click the green ‘plus’ symbol to add a new package. In the new window, name the package, add the gateway address and configure the OS specific settings:
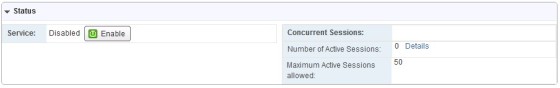
At this point we have configured the interface, an IP pool, private network, authentication settings and configured an installation package to be deployed. With this lot done, we’re ready to enable the SSL VPN-Plus service. On the ‘Dashboard’ menu item, click the ‘Enable’ button:
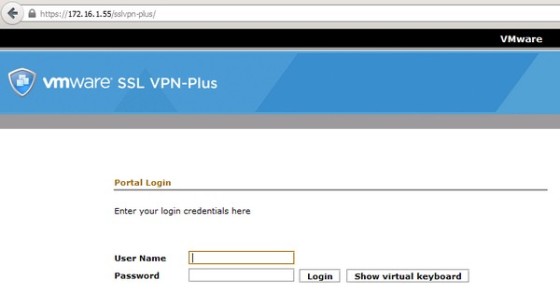
You can test the service by pointing a browser to the ip address /DNS name of the interface on which the VPN service is enabled. You should be presented with a web page:
From here you can log in and download the installation package. Once installed, this software will be used to allow you to connect to the VPN.
Configure Web Access SSL VPN-Plus
SSL VPN-Plus Web Access allows users to access published resources without the need to have a client installed.
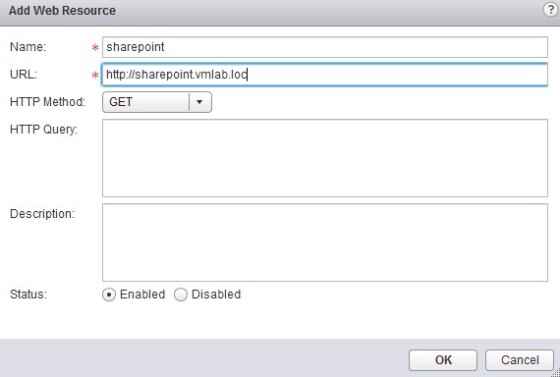
Assuming that configuration for SSL VPN-Plus is in place (see the section above), all that needs to be done is to create the ‘Web Resource’. Go to the ‘Web Resource’ menu item, then click the green ‘plus’ to begin adding a web resource:
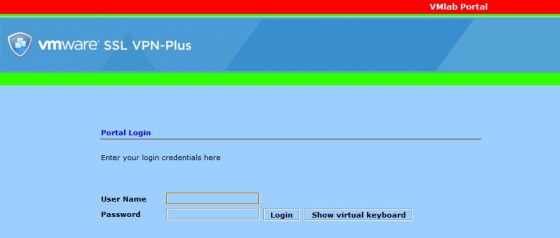
This has been a fairly quick run through of setting up SSL VPN-Plus, but has gone over all the main configuration tasks to get it up and running. There are other configuration options available, such as being able to configure logon and log off scripts, session time out settings, logging and compression amongst others. There is also an option to customize the log on page presented when connecting with a browser. Here’s my updated version – 🙂 :
Luckily, there’s an option to return it to the default colour scheme! Next post, I’ll look at the other VPN types available with NSX – IPSec VPN and L2 VPN.