SSH is disabled by default on ESXi host. In order to connect to a host via SSH you first need to enable the SSH service. In the vSphere client you can do so by navigating to the hosts Configuration Tab, then Software | Security Profile. Click on Services Properties, then select SSH. Click ‘Options’:
You can also enable SSH using PowerCLI or via the CLI, or commonly, using the DCUI:
You should enable SSH only when strictly necessary for troubleshooting purposes. Leaving SSH open creates a security vulnerability, and consumes host resources.
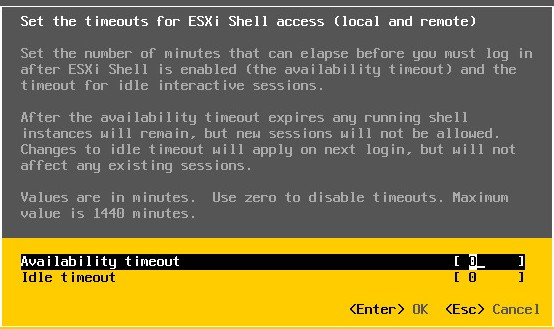
ESXi Shell Timeouts
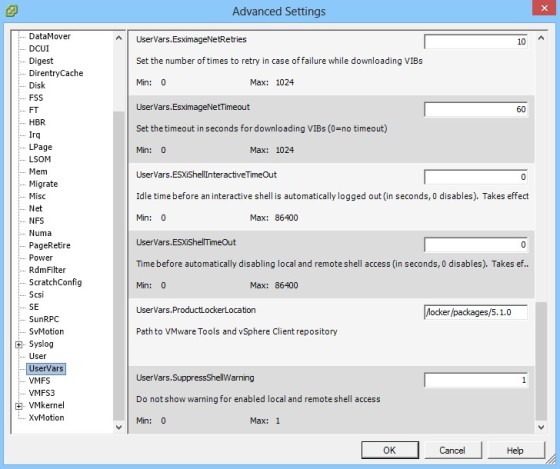
The shell timeout setting allows you to specify how long an inactive session is left open. By default the value is zero, meaning that the session will remain open even if it is inactive. If you change the value to 15 then if the timeout period passes, then the user would have to authenticate again. These values can be set either through the DCUI or as an advanced option on each host, as shown in the screenshots below:
You can also set this options using the CLI:
# esxcfg-advcfg -g /UserVars/ESXiShellInteractiveTimeOut # esxcfg-advcfg -g /UserVars/ESXiShellTimeOut
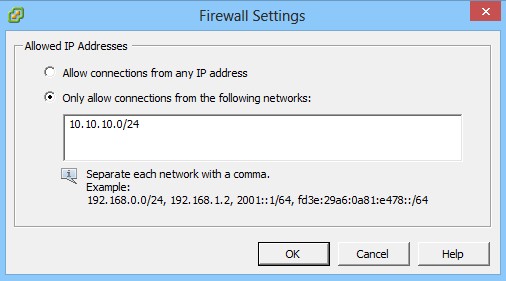
A further way to increase security is to only allow connections from defined IP addresses by editing the SSH Server service firewall rule: