ESXi 5.5 has a new CLI tool for capturing network traffic, which can be used instead of tcpdump-uw. The new tool, pckcap-uw, can capture traffic from uplinks, virtual ports, and vSwitches, unlike tcpdump-uw which allows you to only capture traffic from vmkernel interfaces. I’m not that familiar with pktcap-uw yet, so this post will take a look at what it can do.
To start with, you can get a feel for what the tool can do by looking at it’s help information. As usual, this is accessed using ‘-h’ or ‘–help’:
pktcap-uw --help
The output of this command is quite extensive, so I won’t replicate that here, instead I’ll start by looking at some of the likely common tasks pktcap-uw can be used for.
Capturing VMkernel Interface Traffic
To capture packets being sent and received on a vmkernel interface, vmk0 for example, run:
~ # pktcap-uw --vmk vmk0
The name of the vmk is vmk0
No server port specifed, select 58971 as the port
Output the packet info to console.
Local CID 2
Listen on port 58971
Accept...Vsock connection from port 1025 cid 2
01:35:33.277968[1] Captured at PortInput point, TSO not enabled, Checksum not offloaded and not verified, length 60.
Segment[0] ---- 42 bytes:
0x0000: 0050 56c0 0001 000c 295d a2cf 0806 0001
0x0010: 0800 0604 0002 000c 295d a2cf c0a8 5886
0x0020: 0050 56c0 0001 c0a8 5801
Segment[1] ---- 18 bytes:
0x0020: 0000 0000 0000
0x0030: 0000 0000 0000 0000 0000 0000
This works similarly to the ‘tcpdump-uw -i vmk0’ command. There are a number of filter options available:
Flow filter options, it will be applied when set:
--srcmac
The Ethernet source MAC address.
--dstmac
The Ethernet destination MAC address.
--mac
The Ethernet MAC address(src or dst).
--ethtype 0x
The Ethernet type. HEX format.
--vlan
The Ethernet VLAN ID.
--srcip <x.x.x.x[/]>
The source IP address.
--dstip <x.x.x.x[/]>
The destination IP address.
--ip
The IP address(src or dst).
--proto 0x
The IP protocol.
--srcport
The TCP source port.
--dstport
The TCP destination port.
--tcpport
The TCP port(src or dst).
--vxlan
The vxlan id of flow.
For example, to only capture traffic with a destination IP of 192.168.88.1, you could run:
~ # pktcap-uw --vmk vmk0 --dstip 192.168.88.1 The name of the vmk is vmk0 The session filter destination IP address is 192.168.88.1 No server port specifed, select 59818 as the port Output the packet info to console. Local CID 2 Listen on port 59818 Accept...Vsock connection from port 1026 cid 2
Capturing Traffic on a Physical NIC
You can use pktcap-uw to capture traffic from a host’s physical NICs. For example:
# pktcap-uw --uplink vmnic0 The name of the uplink is vmnic0 No server port specifed, select 9809 as the port Output the packet info to console. Local CID 2 Listen on port 9809 Accept...Vsock connection from port 1028 cid 2
You can also capture traffic from a virtual switchport on a dvSwitch using:
# pktcap-uw --switchport 10
Outputting Captures to a File
You can save the captures to a file for later analysis. To do so, use the ‘-o’ switch followed by a file name:
~ # pktcap-uw --uplink vmnic0 -o /vmfs/volumes/datastore1/capture.pcap The name of the uplink is vmnic0 The output file is /vmfs/volumes/datastore1/capture.pcap No server port specifed, select 10222 as the port Local CID 2 Listen on port 10222 Accept...Vsock connection from port 1029 cid 2 Dump: 47, broken : 0, drop: 0, file err: 0
Pressing CTRL-C will end the capture:
Dumped 345 packet to file /vmfs/volumes/datastore1/capture.pcap, dropped 0 packets. Done.
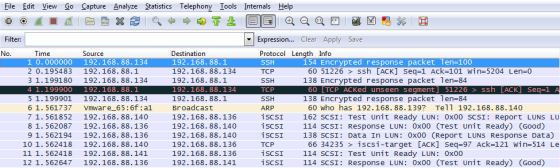
The file can then be downloaded and viewed in a tool such as Wireshark:
If you want to limit how much data is captured you can do so using the ‘-c’ option, which allows you to specify the number of packets you wish to capture:
~ # pktcap-uw --uplink vmnic0 -c 1
The name of the uplink is vmnic0
To capture 1 packets
No server port specifed, select 11196 as the port
Output the packet info to console.
Local CID 2
Listen on port 11196
Accept...Vsock connection from port 1031 cid 2
Receive thread exiting...
03:52:44.885341[1] Captured at EtherswitchDispath point, TSO not enabled, Checksum not offloaded and verified, length 60.
Segment[0] ---- 60 bytes:
0x0000: 000c 295d a2cf 0050 56c0 0001 0800 4500
0x0010: 0028 51c3 4000 8006 7734 c0a8 5801 c0a8
0x0020: 5886 c81a 0016 0473 51ef 1715 7eb7 5010
0x0030: 00fc c8a0 0000 0000 0000 0000
Dump thread exiting...
Destroying session 7
Dumped 1 packet to console, dropped 0 packets.
Done.
Useful Links and Resources
https://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2051814